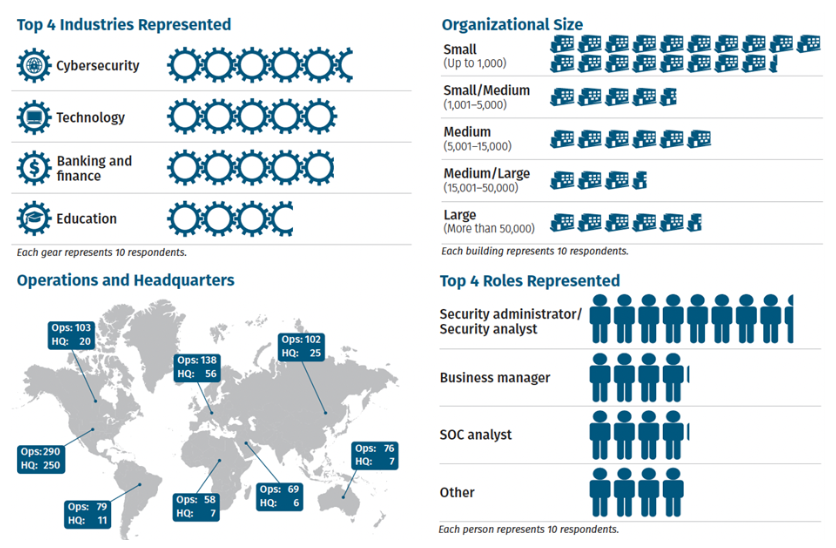
SANS's 2024 Threat-Hunting Survey Review
The 2024 survey highlights a growing maturity in threat-hunting methodologies, with a significant increase in organizations adopting formal processes.
The survey examines the dynamic landscape of cyber threats and the strategies deployed by threat hunters to identify and counteract these risks. Notably, it sheds light on the prevalent types of attacks encountered:
- Business email compromise (BEC): BEC emerges as the foremost concern, with approximately 68% of respondents reporting its detection. BEC involves malicious actors infiltrating legitimate email accounts to coerce individuals into transferring funds through social engineering tactics.
- Ransomware: Following closely behind is ransomware, detected by 64% of participants. Ransomware operations encrypt data and demand payment for decryption, constituting a significant threat in the cybersecurity landscape.
- Tactics, techniques, and procedures (TTPs): The survey found that TTPS are employed in different attack scenarios. In ransomware incidents, threat actors often deploy custom malware, target specific data for exfiltration, utilize off-the-shelf tools like Cobalt Strike, attempt to delete traces, and sometimes resort to physical intrusion into target companies.
The SANS 2024 Threat Hunting Survey highlights the cybersecurity industry's evolution and focuses on improving cyber defense capabilities. Organizations aim to enhance threat hunting with better contextual awareness and data tools, with 51% looking to improve response to nuanced threats.
Nearly half (47%) plan to implement AI and ML to tackle the increasing complexity and volume of threats. There's a significant planned investment in both staff and tools, with some organizations intending to increase their investment by over 10% or even 25% in the next 24 months, emphasizing threat hunting's strategic importance.
Reference: Trend Micro.